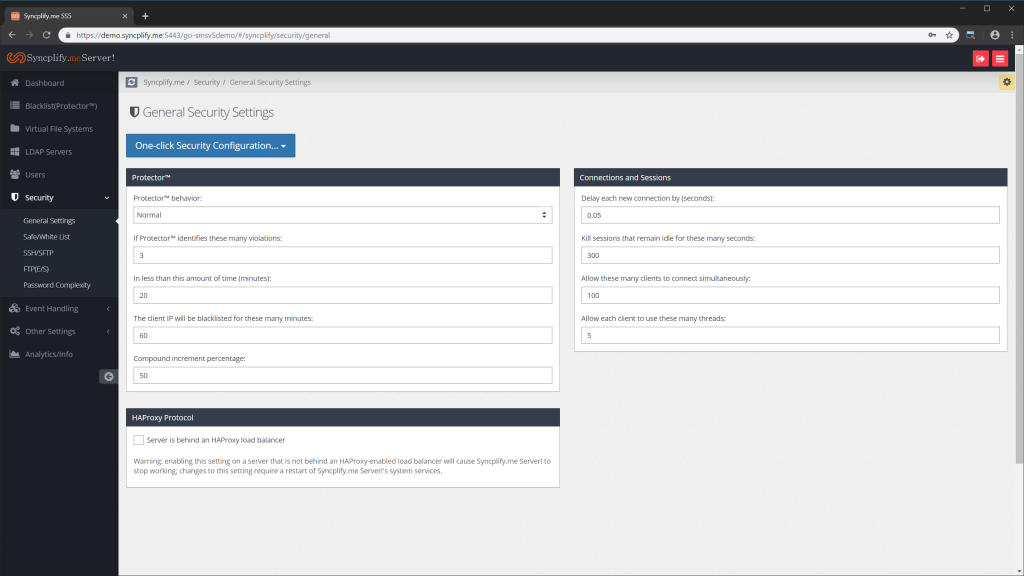
General security settings
The Security->General section of the Configuration Manager contains some of the most important settings of the whole server.
On the left-hand side it contains the configuration for the Protector subsystem:
•Protector behavior:
oIndulgent: allows connect-disconnect sequences with no authentication attempt, therefore it's load-balancer-friendly
oNormal: this is the default settings, and in most cases the best one
oStrict: even minor protocol violations or errors (like requesting the attributes of a non-existent file) can trigger the blacklisting of the client IP - do NOT use this setting if you're using Syncplify.me Server! as backup target for your Cisco UCM because unfortunately that's exactly what the Cisco client does to check whether a file exists or not
oParanoid: this is a zero-tolerance mode, to be used exclusively when you are 100% certain that the client doesn't make any mistake, and never will - even the slightest overlooked detail will trigger the blacklist when Protector is run with Paranoid behavior
•How many errors or protocol violations have to be identified in order to blacklist the client IP
•The time window to look for errors and protocol violations
•The time (in minutes) that a client stays banned once it's blacklisted (0 = permanently blacklisted)
On the right-hand side it contains some connection and session related settings:
•Delay: a short delay to occur every time a client connects - may help dealing with DoS and DDoS attacks more gracefully
•Session timeout: sessions that remain idle for more than X seconds (300 in the example below) will be terminated
•Concurrent clients: this specifies how many different client computers can connect to this virtual server at the same time
•Concurrent connections per client: this specifies how many concurrent operations (typically file transfers) each one of the above client computers can perform - typically many clients (FileZilla, Cisco UCM, ...) perform multiple concurrent connections to ensure the highest transfer speed